

Infoblox Elite Partner
Next-Level Networking
Infoblox has consolidated the management and control of three key core network services, notably DNS, DHCP and IP address management (IPAM), into a single platform that offers the highest standards of security, availability and operational efficiency.
Infoblox provides effective, centralised management and control of DNS, DHCP and other services as well as entire networks of any scale and complexity, regardless of infrastructure. Keep track of your network resources and manage network services centrally and automatically across virtualisation platforms, orchestration and automation tools and cloud service providers. Reduce errors and delays associated with manual interaction.
DNS Security Solutions
Network control technology must provide a maximum of security and a minimal attack surface. Infoblox’s Secure DNS product family includes External DNS Security and DNS Firewall. They offer strong protection against DNS attacks, such as exploits, volumetric attacks or DNS hijacking as well as proactive protection against DNS malware with intelligent fine-tuning.
BloxOne ThreatTM Defence
BloxOne ThreatTM supports security orchestration, automation and response (SOAR) solutions. It shortens the time to investigate and remediate cyber threats, optimises the performance of the entire security ecosystem and lowers the total cost of enterprise threat defence.
Advanced DNS Protection (ADP)
Infoblox’s advanced DNS protection distinguishes between legitimate and malicious DNS traffic in real time. The DNS server responds only to valid queries, even if it is under attack. ADP provides protection against volumetric attacks, including DDoS and TCP/UDP/ICMP floods, as well as DNS hijacking, cache poisoning and other DNS-specific attacks.


Expert Partner and Certified Technology Expert
Fortinet’s comprehensive product portfolio can fully protect the IT infrastructure of an enterprise against external and internal threats. Fortinet’s highly reliable products are equipped with specially designed hardware and optimised using security processors and acceleration components (ASIC) developed in-house. The portfolio ranges from FortiGate Next-Generation Firewalls to Fortimanager centralised management and logging to FortiAP wireless solutions and FortiMail email security.
The high quality of its products has earned Fortinet several top rankings in the Gartner Quadrant. Fortinet’s products and solutions combine award-winning network and data security as well as secure access products that share information and work together in the Security Fabric.
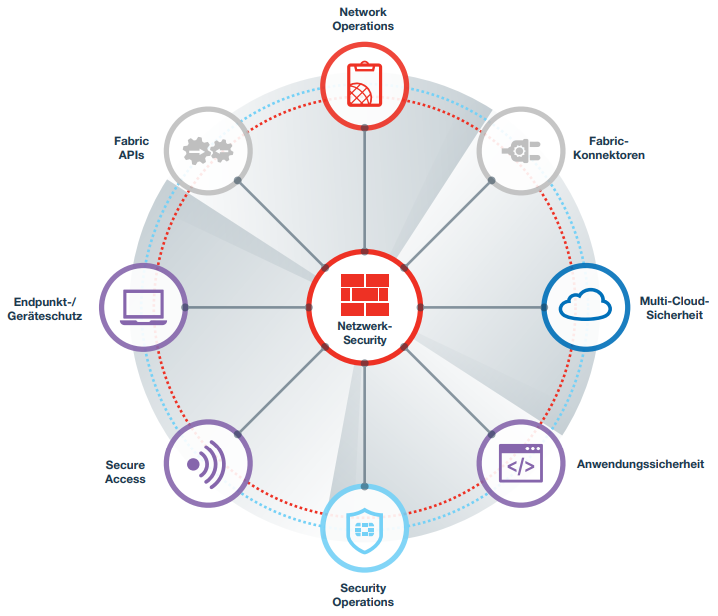
Security Fabric
The Security Fabric combines the entire range of security technologies in one platform and is an integral part of the network. It offers superior protection against new and known threats.
FortiGate – Next-Generation Firewall
The FortiGate series offers a wide selection from large data centre firewalls with more than 1,000 Gbps throughput and 100 Gbps interfaces to small SOHO desktop units. What they have all in common is their uniform operation, good hardware architecture with hardware accelerators and a wide range of functions from firewalling for IPv4 and IPv6, VPN, SSL-VPN, application control, anti-virus, URL filtering, intrusion prevention (IPS), integrated WLAN controllers and many more useful features.
There are also virtual appliances for VMware ESXi, Microsoft Hyper-V, KVM and Citrix XENserver and cloud integration.


NUTANIX Scaler Partner
Hyper-Converged Infrastructure
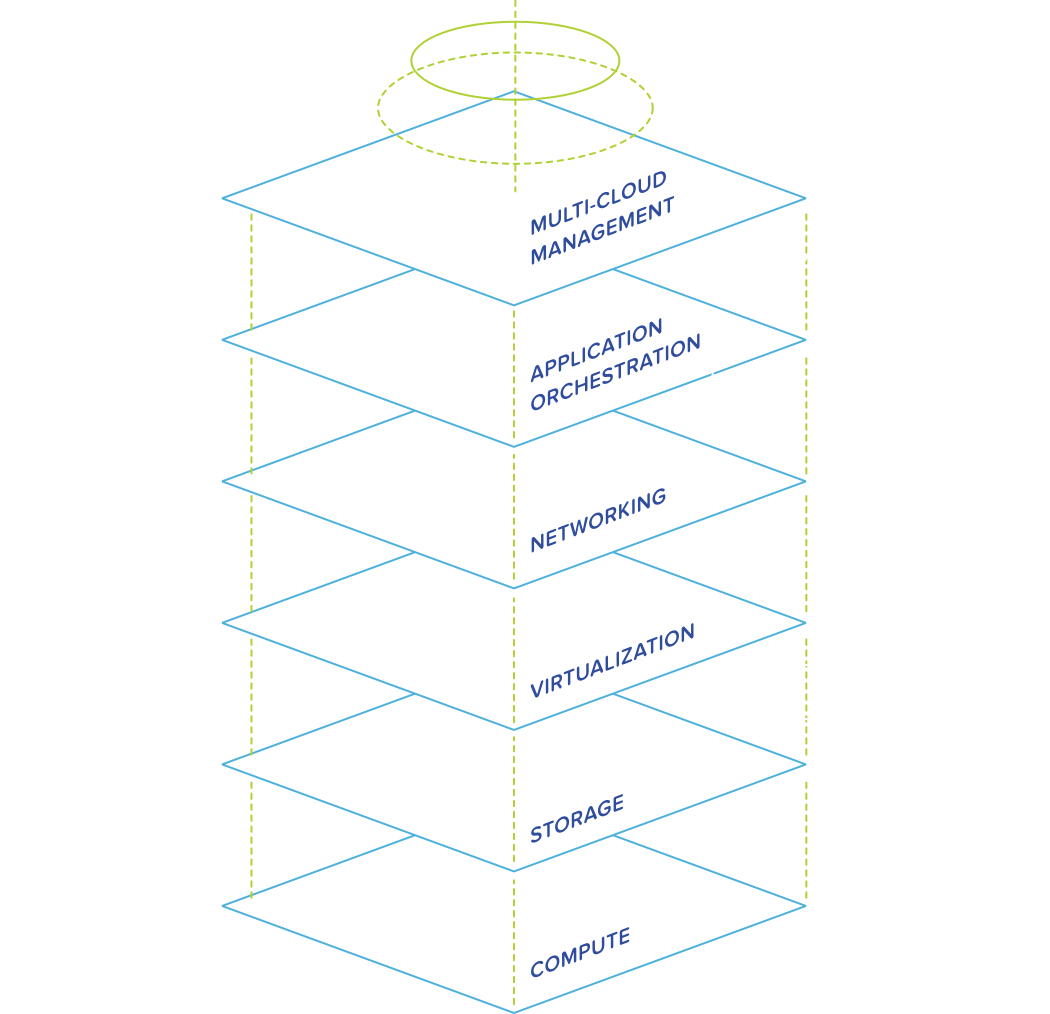
Nutanix solutions are based on HCI technology (hyper-converged infrastructure), which is popular throughout the industry. It is a comprehensive software platform that can be deployed anywhere, modified at any time and taken to where it is needed: on premises, in the cloud, a combination (hybrid cloud) or multiple clouds (multi cloud). It integrates computing, virtualisation, storage, networking and security and supports applications of any scale, whether on premises or in the cloud.
Nutanix software and cloud services harmonise IT operations and ensure smooth application mobility across different cloud environments. Nutanix combines public cloud simplicity and agility with private cloud performance, security and management.
- Complete cloud environment – integration of all computing, virtualisation, storage and networking resources
- Centralised management – control of data centre infrastructure, applications and clouds via a user-friendly central dashboard
- Rapid deployment of applications – applications or virtual desktops can be deployed in short time
- Automated application management – automation of daily IT tasks
- Cost reduction – reduction of total cost of data centre operation by up to 60%
- True hybrid cloud – combination of private and public cloud processes through unified management
Nutanix Hyper-Converged Infrastructure (HCI)
Nutanix is a so-called hyper-converged infrastructure (HCI) solution that runs on different types of individual servers (nodes). All these servers are interconnected through the HCI software platform. The processors, internal memory, hard disks (storage) and network interfaces are bundled in clusters on which virtual machines are run.
The distribution of data, applications and the entire workload across multiple servers makes the HCI platform particularly powerful. Due to the integrated data replication on the servers – even across two locations – failure safety is very high. If one of the nodes fails, the availability of the platform and applications is not affected.
The hardware is very easily scalable. Since a node contains all the required components, an existing cluster can be expanded within a very short time. This means that the Nutanix infrastructure grows with the enterprise. It takes just a few clicks to update the entire cluster, including firmware upgrade of all servers, without downtime.
Nutanix works closely with other hardware manufacturers to give its customers the greatest possible freedom of choice. Cisco, Dell, Fujitsu, HPE, Huawei, Lenovo and several others all offer Nutanix-certified hardware. Moreover, hardware from various manufacturers can be combined to form a large cluster, or products such as Infoblox can be integrated.
The solution is also open in terms of the hypervisor. Hyper-V ESXi and Nutanix’s own AHV are supported. The latter is based on KVM and is included in the product without additional licence fees.


Gold Partner
Network Security Policy Orchestration
Tufin® is market leader in network security policy orchestration
Tufin enables enterprises to centrally manage, visualise and control security policies in hybrid environments (cloud, physical networks and virtualised infrastructures).
The award-winning Tufin Orchestration Suite™ is a full policy-focused solution for automated planning, implementation and control of network security changes. Enterprises choose Tufin to achieve high agility in a constantly changing environment with multi-faceted requirements while maintaining a robust security posture. Network security automation allows organisations to implement security changes within minutes rather than days, with continuous compliance and increased agility.
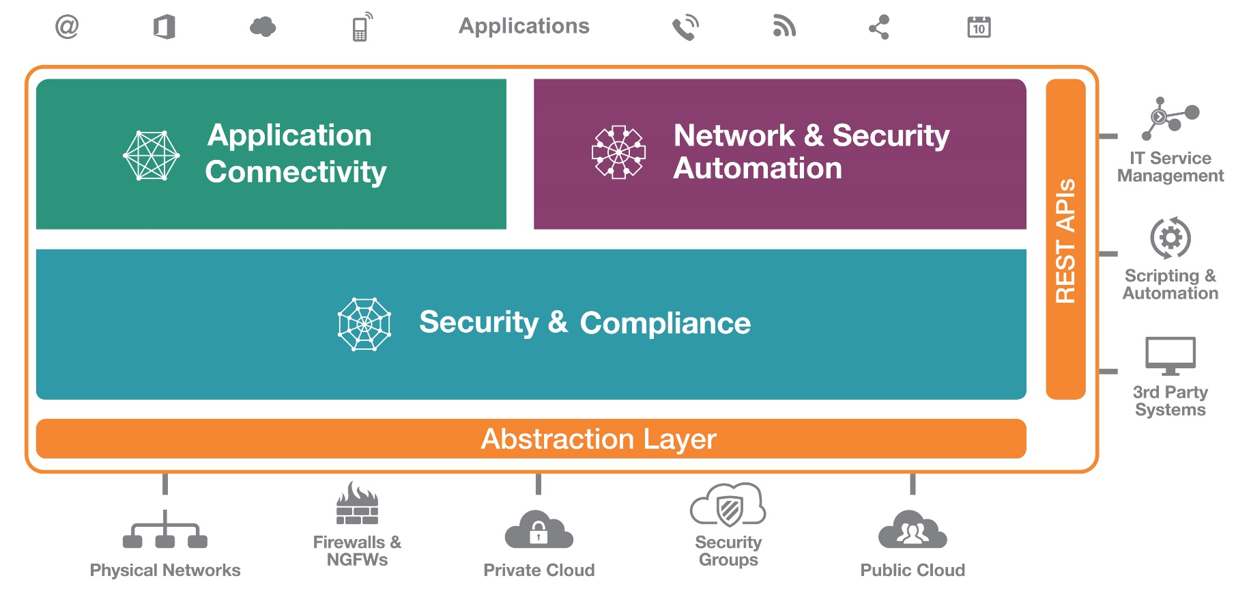
SecureTrack – Firewall Management Solution
- visibility, even in complex, distributed environments
- automatic documentation of any policy changes
- optimisation of existing policies
- reporting, audit & compliance
- Unified Security Policy (USP)
SecureApp – Visibility and Control
- bridge between DevOps teams and network teams
- visibility through end-to-end relationships of applications
- migration planning
- documentation of connectivity of applications
SecureChange – Change Management
- clear definition of change workflows
- change analysis with USP
- policy fesign
- optional provisioning
- automatic documentation in combination with SecureTrack
- sensible extensive automation of changes


Gold Partner
Transparency and Control over your Network
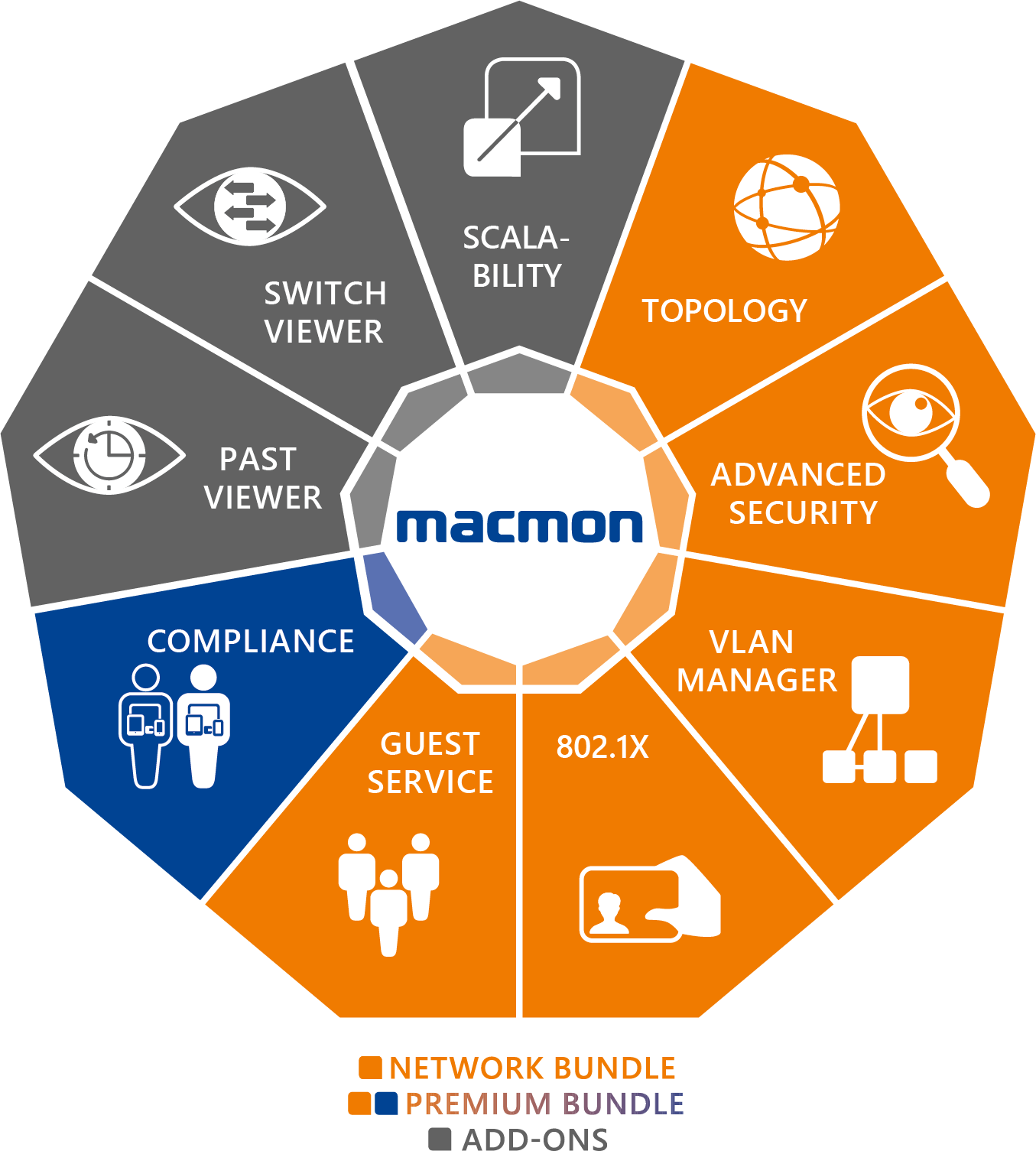
macmon’s NAC (Network Access Control) solution provides complete insight into your network environment. You are always in control and know which devices are in your network and where they are located. macmon identifies all systems connected to your network and monitors them efficiently.
Company devices can very easily be authenticated via the local database or a centralised identity source (e.g. Active Directory) and authorised by macmon to access the networks defined for the end device group, regardless of whether the device connects via WLAN or the wired network.
Guests and personal devices (BYOD) can easily and securely be authorised via the guest portal using dynamic management of the network segments.
macmon’s NAC solution is easy to implement and offers the possibility to integrate solutions of numerous third-party manufacturers.
Overview of macmon’s product bundles:
- Network bundle: efficient protection of network access
- Premium bundle: expansion of the network bundle with comprehensive mechanisms for checking the compliance/security status of end devices and the rapid enforcement of security policies.
- Add-ons: expansion of network management functions for increased security


Gold Partner
Reliably integrable solutions for mail traffic

SEPPmail has been offering reliable and easy-to-integrate solutions for secure mail traffic for more than ten years. The secure e-mail solution of the Swiss company SEPPmail includes all functions to protect the sending of confidential data by e-mail, to guarantee the authenticity of the sender and to secure the confidentiality and integrity of the message.
Each SEPPmail appliance can be configured and seamlessly expanded based on customer-specific requirements. Your choice ranges from entry-level solutions to comprehensive secure e-mail platforms.
Secure E-Mail Communication
Whether as a VM or as an appliance, SEPPmail handles the encryption and signing of e-mail communication. The internal certification management can be automated to a large extent. It manages the import of self-signed S/MIME and PGP certificates as well as the creation or request of certificates for new users. The cluster capability guarantees robust and interference-resistant e-mail communication.
Secure E-Mail Gateway
SEPPmail’s Secure E-Mail Gateway, which has repeatedly won awards, is convincing due to its functionality, simplicity and flexibility.
It handles key management without any administrative effort for the administrator and autonomously determines the most suitable encryption method for the recipient. The following methods are supported:
- patented GINA encryption
- domain encryption
- OpenPGP encryption
- S/MIME encryption
- TLS encryption
Further Products
- domain encryption
- digitale signature
- individual encryption
- centralised disclaimer management


Certified Partner
Cloud Data Management and Backup
Rubrik makes it easier for organisations all over the world to handle their data and keep it safe. Rubrik offers a wonderfully simple product for companies to address their data management challenges and requirements. Their experience from the point of view of end customer and enterprise offers a fresh approach to solving a tiresome: backup and recovery.

Rubrik Cloud Data Management


Innovator Partner
Palo Alto is shaping the cloud-centric future with technologies that are transforming the way people and organisations work.
![]()
Enterprise Security
One single platform that unifies the products essential for the IT security of an enterprise. Using this platform results in simplified and highly effective interconnection and security of the IT environment.
- next-generation firewalls
- cloud access security
- security subscriptions
- network security management
![]()
Cloud Security
Prisma™ Cloud provides complete security throughout the entire development lifecycle in any cloud so that you can develop native cloud applications with confidence.
- comprehensive native cloud security
- complete lifecycle
- across any cloud
- AWS, Microsoft Azure, Google Cloud
![]()
Security Operations
Prevent everything that can be prevented. Detect and quickly investigate anything that cannot be prevented.
- Cortex XDR
- Cortex XSOAR
- Cortex Data Lake
- AutoFocus


Microsegmentation
Guardicore is a data centre and cloud security provider. As part of the Guardicore Centra Security Platform, it fills the gap in application visibility that most organisations have today. Guardicore’s segmentation solution integrates deep, granular visibility across the IT infrastructure. It incorporates network and application flows in combination with real-time detection and response to security breaches across the entire data traffic and all applications. Guardicore offers more security and visibility in the cloud, in the data centre and at the endpoint. With Guardicore, segmentation projects are affordable and can be implemented within short time. The software-only approach is decoupled from the physical network and offers a faster alternative to firewalls.
Guardicore Centra
“The fastest way to visualise and segment your assets in the data centre, the cloud or a hybrid cloud infrastructure.” www.guardicore.com
The Centra security platform uses software-based segmentation to achieve a higher security standard faster and easier without disrupting operations.
- Granular visibility: mapping of network and application flows down to the process level with real-time detection and historical data. Abstraction with the help of labels.
- Platform independence: microsegmentation across any combination of legacy systems, bare metal servers, VMs, containers or cloud instances.
- Policy enforcement: definition and enforcement of policies at the network, workload, user, device and process levels to isolate and segment critical applications and infrastructure.
- Comprehensive use case support: supports the widest range of use cases for segmentation and microsegmentation – from environment segmentation (DEV/TEST/PROD) to application ring-fencing.
- Wide protection: built-in capabilities to detect and respond to security breaches.


Unleash the Power of Arista Switches: Empowering Your Network Infrastructure
With Arista switches, you enter a new dimension of network performance. These switching solutions offer an exceptional combination of speed, reliability, and scalability.
Whether you are a small business in need of a reliable network for daily operations or a large data center processing massive amounts of data, Arista switches have you covered. Their innovative architecture and advanced features enable seamless connectivity and optimal performance within your network infrastructure.
Arista switches provide incredibly fast transmission speeds to efficiently handle your data traffic. With flexible configuration options, these switches can be customized to meet the specific requirements of your organization. Additionally, they offer high reliability and enhanced security features to protect your data and secure your network against unauthorized access.
At the heart of Arista switches lies their state-of-the-art architecture, designed to handle the most demanding workloads. Equipped with high-speed ASICs (Application Specific Integrated Circuits), these switches deliver lightning-fast data processing, ensuring minimal latency and maximizing network efficiency.
With an intuitive user interface and easy configuration, Arista switches enable quick deployment and simplify network operation and management. They also support modern network standards, ensuring future-proof performance in the years to come.


Premium Partner
Identity Protection and Anti-Fraud Solutions
OneSpan (formerly Vasco) is a leading provider of cyber security technology. OneSpan’s solutions range from risk-based adaptive authentication to digital identity verification and are delivered on a cloud-based platform. They focus on verified identities, intelligent prevention of fraud, secure account opening and transactions and signing of documents with eSignatures. Using OneSpan’s solutions, you can make the use of digital platforms secure and convenient for your users.
Sidarion focuses on the authentication solutions of OneSpan’s product portfolio:
- Intelligent adaptive authentication: orchestration to detect, authenticate and reduce fraud, and optimise the digital experience
- Mobile security suite: app security and authentication functions
- Mobile authenticators: increase security through two-factor authentication with mobile devices
- Authentication server: full management of passwords and tokens in a single integrated system
- Hardware authenticators: user-friendly Digipass hardware authenticators to secure remote access


Menlo Provides Security Through Isolation
Menlo is pursuing a novel approach in fighting cyberattacks such as malware or phishing. The Menlo Security Isolation Platform (MSIP) provides a way to intercept malware before it can even reach the user.
Isolation Instead of Detection
The solution eliminates web-based malware (from websites, e-mails, documents) by redirecting it to the MSIP and isolates the client from any malicious content. There is a significant reduction in time-consuming analyses of threat reports and support efforts as found in detection systems.
The MSIP assigns each web request from the user to a dedicated virtual container (DVC), a secured virtual environment. The operating system on the isolator then forwards the request to the internet.
The target website’s response to the user request is accepted by the isolation platform and executed in the browser within the DVC. If it is malicious code, it cannot cause any damage. As soon as malware tries to access processes or files without authorisation, the isolator and all its contents are deleted, forensic data is logged and an alarm is triggered.
The MSIP integrates into the infrastructure like a classic web proxy and e-mail MTA solution. Any kind of executable web content, such as Java or Flash, will be converted into HTML 5 by the Adaptive Clientless RenderingTM (ACR) technology. The user thus receives an image of the requested website. The user’s browser experience is not affected.
Menlo’s product portfolio includes three solutions that can be combined but are also available individually:
- Web isolation service
- Document isolation service
- Phishing isolation service
Keine zusätzliche Software auf dem Endgerät
Entlastung des Security Teams da die Analyse der Gefahren wegfällt
100% sichere Isolation des Clients vor schädlichen Inhalten (auch Bilder und Fonts)
Entfernt Java und Flash vom Browser
Schutz vor Phishing-Attacken
Als Cloud oder on-prem Lösung (VM)
Lizenziert pro User und Jahr


Cloud Security Everywhere Your Employees Go
The next-generation Bitglass Cloud Access Security Broker (CASB) solution enables your organisation to leverage the cloud while ensuring data security and regulatory compliance. Bitglass secures your data across every cloud application and device.
The CASB solution enables you to implement threat protection and contextual control of data access from any device, even unmanaged devices. With Bitglass, organisations may even selectively delete data from lost, stolen or unmanaged devices.
The Bitglass Zero-day CASB CoreTM uses machine-learning techniques to deliver real-time data and threat protection across the dynamic enterprise cloud footprint. The platform automatically learns and adapts to new cloud applications, malware threats, behaviours and more – for every application and device.

- Securing sensitive data in managed cloud applications: comprehensive control and transparency for each managed application (including access control, data leak prevention, malware protection, user behaviour analysis)
- Data leak prevention in unmanaged cloud applications: control via user interaction with any cloud application such as Facebook, Dropbox or LinkedIn. Users can view and interact with these applications. However, content upload is prevented.
- Protection of personal devices (BYOD): Bitglass’ patented agentless mobile data protection provides control over corporate data and applications on personally managed devices. Automated, transparent provisioning requires no intervention from the IT department or staff.
- Detect and respond to suspicious activities: detect and prevent abnormal user behaviour. A hacker’s login from new devices or locations or attempts at downloading unusually large amounts of data from a cloud application can be blocked.
- Rapid deployment of architecture: Bitglass’ unique, agentless next-gen architecture enables rapid deployment at large scale while maintaining end user privacy.


Reduce the risk across your entire environment. Rapid7’s cloud platform offers full visibility, analytics and automation capabilities so that you can monitor vulnerabilities, detect suspicious activities, investigate and prevent attacks and automate your tasks with ease.
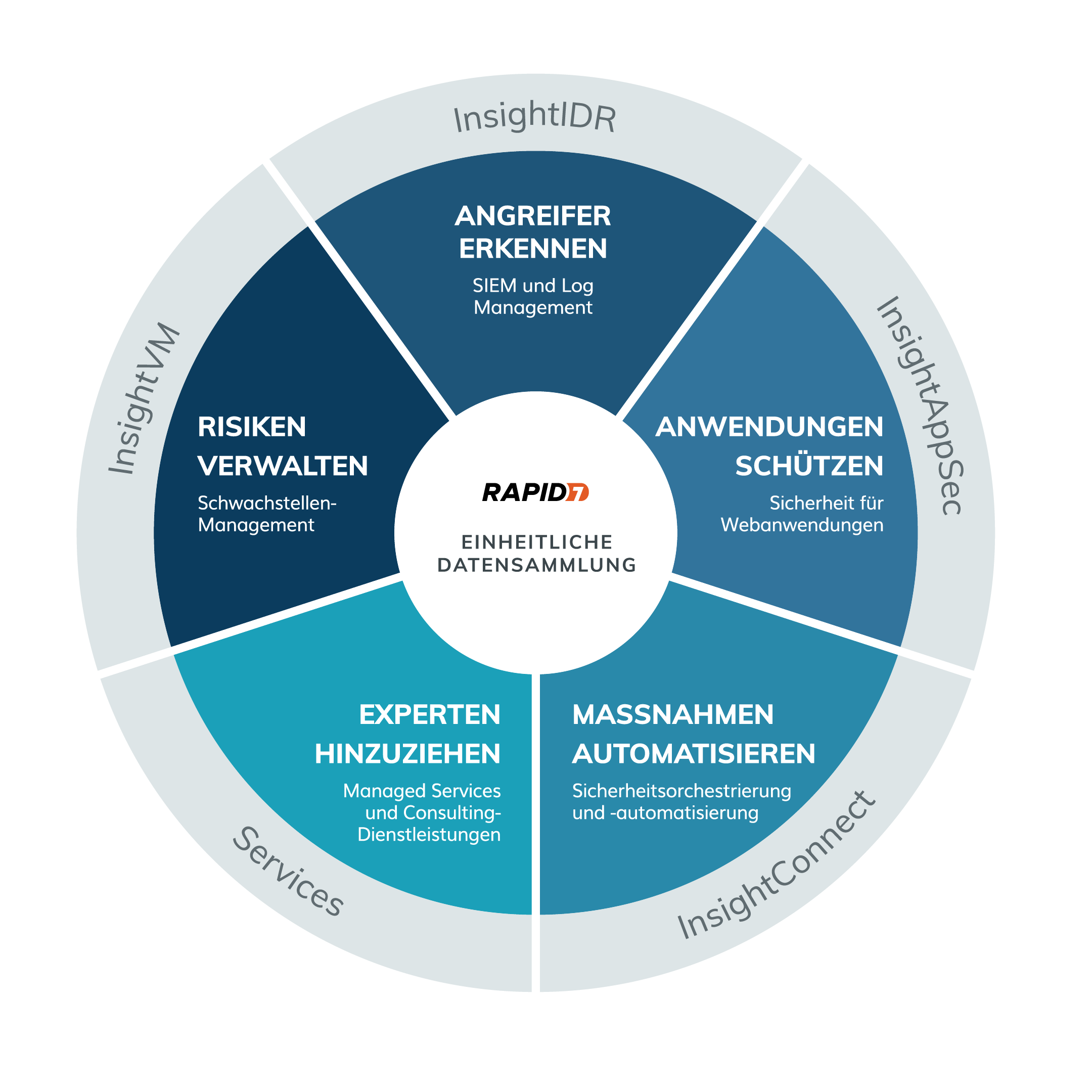
- InsightVM: vulnerability management
- InsightIDR: user behaviour analysis and SIEM
- InsightAppSec: application security
- InsightConnect: orchestration and automation
- InsightOps: logging management
Enterprise Level Solution Provider
Virtualised Server Infrastructure
VMware is our customers’ preferred software for virtualising their server infrastructure. The portfolio ranges from the free hypervisor ESXi to the suite to manage and automate complex processes and architectures in your data centres. In combination with a Nutanix converged cluster, we achieve a very stable and simple operation of your IT environment.

PRODUKTE
vSphere

VMware vSphere® ist die weltweit führende Virtualisierungsplattform zum Aufbau von Cloud-Infrastrukturen.
Leistungsstarkes Computing:
Virtualisieren Sie Ihre x86-Serverressourcen und aggregieren Sie sie in logischen Pools für die Zuweisung mehrerer Workloads.
Netzwerkservices
Profitieren Sie von optimierten Netzwerkservices für virtuelle Umgebungen sowie von vereinfachter Verwaltung und vereinfachtem Management.
Hohe Sicherheit
Schützen Sie Ihre Daten und Anwendungen mit der sichersten Bare-Metal-Virtualisierungsplattform der Branche.
Hochverfügbarkeit
Maximieren Sie die Betriebszeit Ihrer gesamten virtualisierten Infrastruktur, reduzieren Sie ungeplante Ausfallzeiten und eliminieren Sie geplante Ausfallzeiten für Server- und Storage-Wartung.
Konsistente Automatisierung
Senken Sie Betriebsausgaben und minimieren Sie Fehler durch die Optimierung von Routineaufgaben mit den präzisen und zuverlässigen Lösungen von vSphere.
NSX
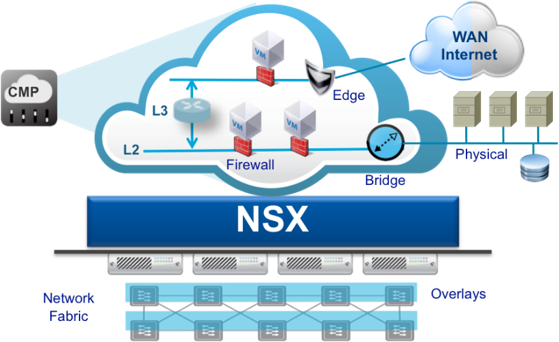
VMware NSX ist die Netzwerk-Virtualisierungsplattform für das Software-Defined Datacenter (SDDC)
NSX integriert Netzwerk- und Sicherheitsfunktionen, die üblicherweise von der Hardware übernommen werden, direkt in den Hypervisor. Ähnlich wie die Servervirtualisierung vor 10 Jahren transformiert die NSX-Plattform für Netzwerkvirtualisierung das Betriebsmodell des Rechenzentrumsnetzwerks grundlegend und hilft Tausenden Kunden dabei, das Potenzial des SDDC voll auszuschöpfen.
NSX bildet die gesamte Netzwerkumgebung als Software ab. NSX stellt umfassende logische Netzwerkelemente und -services bereit wie logisches Switching, Routing, Firewalling, Lastausgleich, VPN, QoS und Überwachung. Virtuelle Netzwerke werden programmatisch bereitgestellt und unabhängig von der zugrunde liegenden Hardware verwaltet.
Netzwerk-Mikrosegmentierung
Mit automatisierten, detaillierten Richtlinien, die mit den virtuellen Maschinen verknüpft sind, sorgt NSX für mehr Sicherheit innerhalb des Rechenzentrums. NSX ermöglicht Mikrosegmentierung und dämmt so die laterale Ausbreitung von Bedrohungen innerhalb des Rechenzentrums erheblich ein. Da Mikrosegmentierung mit NSX aus betrieblicher Sicht sinnvoll wird, ermöglicht NSX ein grundlegend besseres Sicherheitsmodell im Rechenzentrum.
Horizon

VMware Horizon™ bietet virtualisierte und Remote-Desktops und Anwendungen über eine einzige Plattform und ermöglicht Anwendern Zugang zu allen ihren Windows- und Online-Ressourcen über einen einheitlichen Arbeitsbereich.
Bereitstellung von Desktops und Anwendungen über eine einzige Plattform
Stellen Sie virtuelle oder Remote-Desktops und Anwendungen über eine einzige Plattform bereit, um das Management zu optimieren und Anwender einfach zu berechtigen.
Einheitliche Arbeitsumgebung mit großartiger Anwendererfahrung
Sichere Bereitstellung von Desktops, Anwendungen und Onlineservices für Anwender in einer einheitlichen Arbeitsumgebung. Einheitliche Anwendererfahrung – unabhängig von Gerät, Ort, Medien und Art der Verbindung
Zentrales Image-Management
Zentrales Image-Management für physische, virtuelle und BYO-Geräte.
„Closed Loop“-Management und -Automatisierung
Konsolidierte Kontrolle, Bereitstellung und Sicherheit von Anwender-Computing-Ressourcen mithilfe von Cloud-Analysefunktionen, -Automatisierung und -Orchestrierung sowie Self-Service für die Cloud.
Optimiert für das Software-Defined Datacenter
Dynamische Zuweisung von Ressourcen mit virtuellem Storage, virtuellem Computing und virtuellen Netzwerken, um Desktop-Services nach Bedarf einfach und kostengünstig bereitstellen zu können


Redefinition of Cloud, Network and Data Security
Netskope’s Security Cloud unifies security and network solutions on a single platform with a single management console and policy framework for all products:
- Next Gen SWG (inkl. CASB)
- Zero Trust Network Access
- Cloud Firewall
- SSPM/CSPM
- Advanced Data Protection
- Advanced Threat Protection
- Borderless SD-WAN
Netskope’s Private Cloud infrastructure, with its own data centers, is present in 70 regions worldwide and is the third-largest peering network in the world. All regions are available to Netskope’s customers at no additional cost and offer full functionality. With Netskope’s data centers in Geneva and Zurich, you also have the option to keep your data within national borders..
Netskope was selected by Gartner as a market leader for Security Service Edge in April 2023. Netskope has particularly surpassed its competitors in the areas of “Securing Remote Workers” and “Protecting Sensitive Data”.
