Principle of least privilege
The idea of the “principle of least privilege” has been known for a long time and is used in many areas. Various IT security topics have become better known under the Zero Trust hat in recent years:
- Microsegmentation (network-related): Or even nano-segmentation, where the initiating process is also taken into account.
- Least privilege access rights (identity-related): So not only where, but also who and what can be accessed.
Google also contributed to the above-mentioned topics with the BeyondCorp security model.
With regard to microsegmentation, different approaches have been established:
- Infrastructure-based
- Host-based
Focus on host-based micro-segmentation
The advantage of the host-based variant is that it is infrastructure agnostic. Host-based firewalling can support hybrid clouds (AWS, Azure, Nutanix, bare metal) with just one solution.
Segmentation from the infrastructure, on the other hand, is the more classic option, which is generally more trusted.
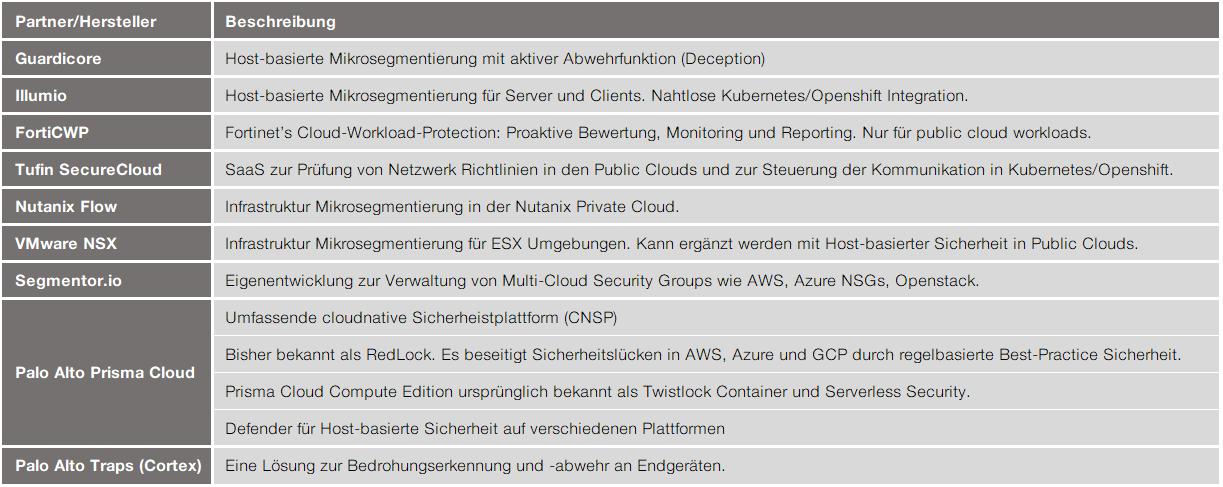
Some of our manufacturers and partners already offer Zero Trust products. In the following you will get an overview of the offer from our portfolio:
So today we are much further along in terms of Zero Trust technologies.
But when we turn the screw with network segmentation, automation of certain processes is required for a sustainable operational load.
We would be happy to advise you in order to find the best solution for your requirements.
Senior Security Engineer
Mario Gersbach
For further information please contact us at support@sidarion.ch or +41 43 544 10 66.
Related Links:
https://www.guardicore.com/
https://www.tufin.com/blog/zero-trust-model-five-step-approach
https://segmentor.io/